Fadi Mohsen
I joined the Department of Computer Science at RUG as a Postdoctoral Fellow in summer 2019. In May 1, 2022 I started a new position with the CS department as an Assistant Professor. Prio to joining RUG, I had been in the Department of Computer Science, Engineering and Physics at University of Michigan-Flint as an Assistant Professor.
Recent Projects
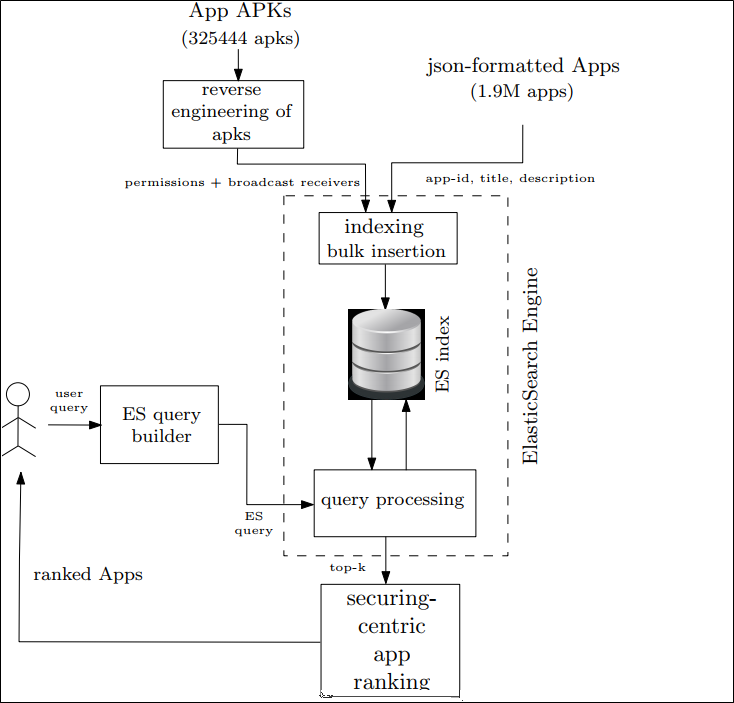
Countering Intrusive Mobile Apps
In this project, we are proposing and evaluating a new security-centric ranking algorithm built on top of the Elasticsearch engine to assist users evade installing intrusive apps. The algorithm calculates an intrusiveness score for an app based on its requested permissions, received system actions, and on the privacy preferences of users. In doing so, we are proposing a new approach to capture users’ privacy preferences. The approach is evaluated through an online user study. The ranking algorithm is being evaluated on a large corpus of Android apps contextual data and APK files by conducting a pilot study and benchchmarking study. The results show that the scoring and reranking steps add very small overhead. Moreover, participants of the online and pilot studies gave positive feedback for the ranking algorithm and privacy preferences solicitation approach. The results suggest that our proposal would definitely protect the privacy of mobile users and pushes developers into requesting the minimum privileges that are required for their apps to function.
View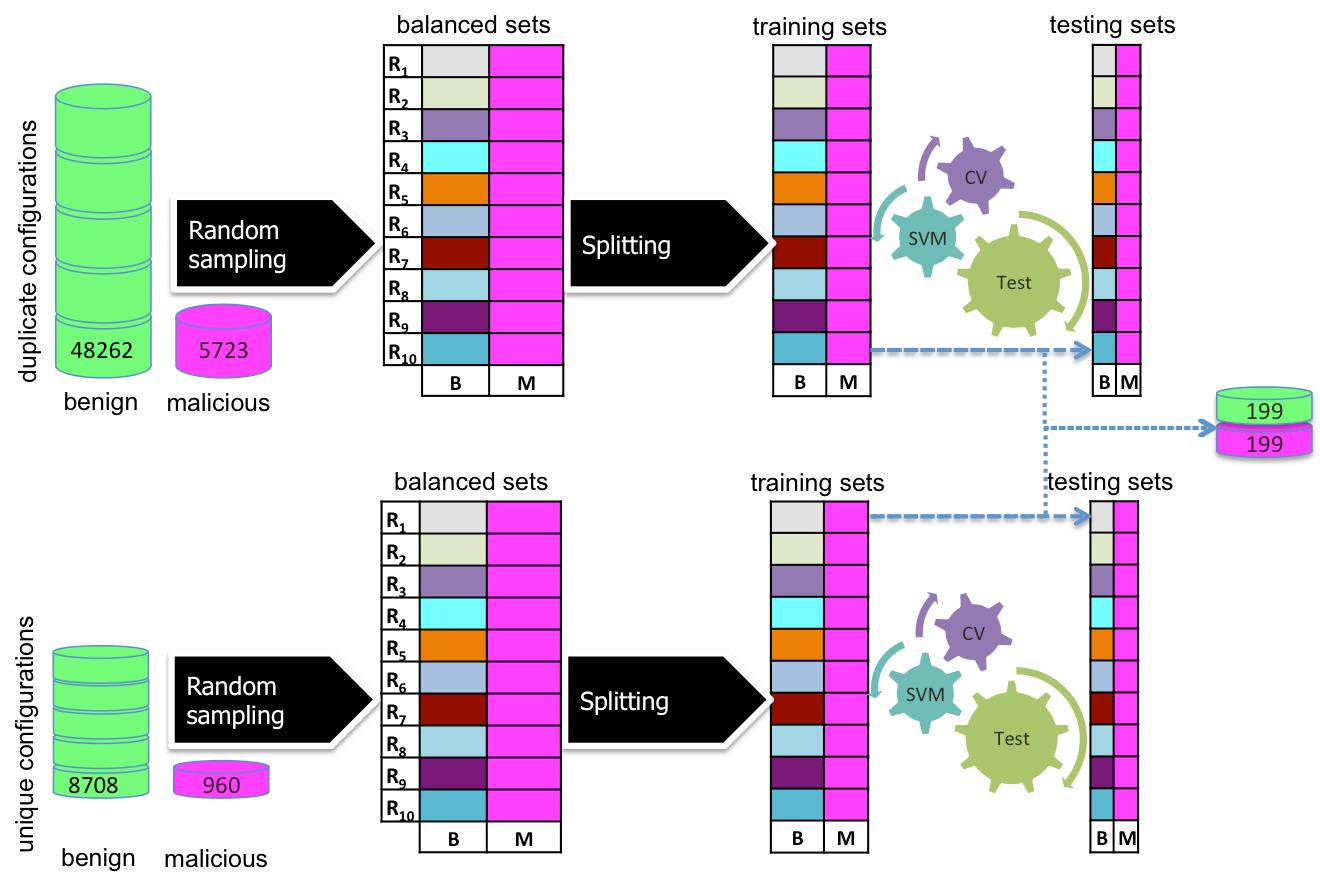
Detecting Android Malwares by Mining Statically Registered Broadcast Receivers
In this paper, we are conducting an empirical study to investigate the usage patterns of the Broadcast receivers component by malicious and benign Android applications. In addition to processing the AndroidManifest. xml files, the source code of malware samples, in particular the onReceive() are manually analyzed. We also propose a data mining malware detection mechanism based on the statically registered Broadcast receivers. Our research shows that Android Broadcast receivers are intensively used by malware compared to benign applications. Our Java code analysis shows that malware samples fully utilize Broadcast receivers compared to benign apps. Finally, our experiments showed that using the Broadcast receivers with permissions improves the malwares prediction accuracy..
View
Quantifying Information Exposure by Web Browsers
Internet surfing entails exchanging numerous HTTP requests between clients and servers. Attached with each request is a string containing plenty of information about the client called User-Agent string. There have been numerous researches that showed the privacy and security risks of User-Agent strings. In this work we aim to minimize those risks by directing users towards using less exposing browsers. In doing so, we propose and test a new method for calculating an exposure score for web browsers based mainly on their User-Agent strings besides other attributes. We then apply this method on a dataset of over a million browsers to infer and compare their exposure scores. Finally, we present a demo web tool that shows how the resulting scores can be leveraged to aid end users. Our results reveal a variation in the exposure scores of these browsers, which creates prospect for safe Internet surfing..
View